How To Find A Command And Control Service Traffic In Pcap File
This post is also available in: 日本語 (Japanese)
When reviewing bundle captures (pcaps) of suspicious activeness, security professionals may demand to consign objects from the pcaps for a closer test.
This tutorial offers tips on how to export dissimilar types of objects from a pcap. The instructions presume y'all sympathise network traffic fundamentals. We will use these pcaps of network traffic to practice extracting objects using Wireshark. The instructions likewise assume you lot have customized your Wireshark cavalcade display as previously demonstrated in this tutorial.
Warning: Most of these pcaps contain Windows malware, and this tutorial involves examining these malicious files. Since these files are Windows malware, I recommend doing this tutorial in a not-Windows surround, like a MacBook or Linux host. You could also use a virtual machine (VM) running Linux.
This tutorial covers the following areas:
- Exporting objects from HTTP traffic
- Exporting objects from SMB traffic
- Exporting emails from SMTP traffic
- Exporting files from FTP traffic
Exporting Objects from HTTP Traffic
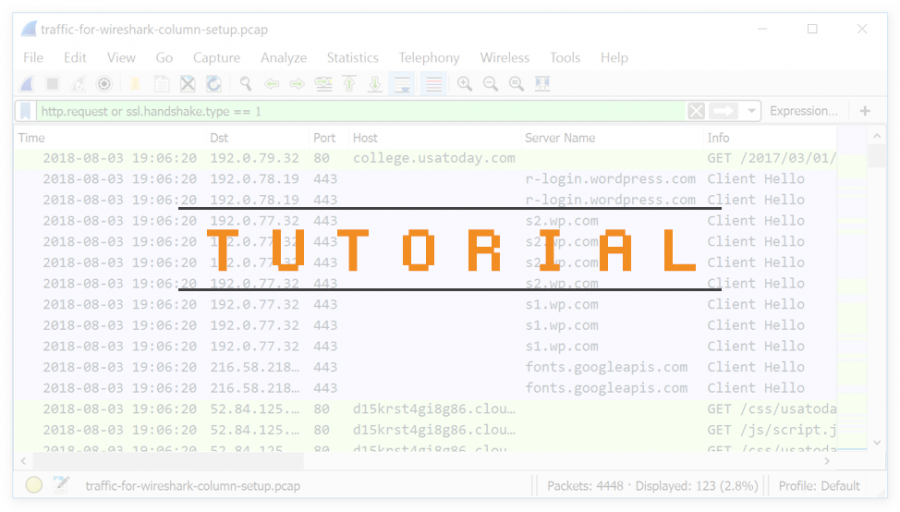
The first pcap for this tutorial, extracting-objects-from-pcap-example-01.pcap , is bachelor hither. Open the pcap in Wireshark and filter on http.request as shown in Effigy 1.
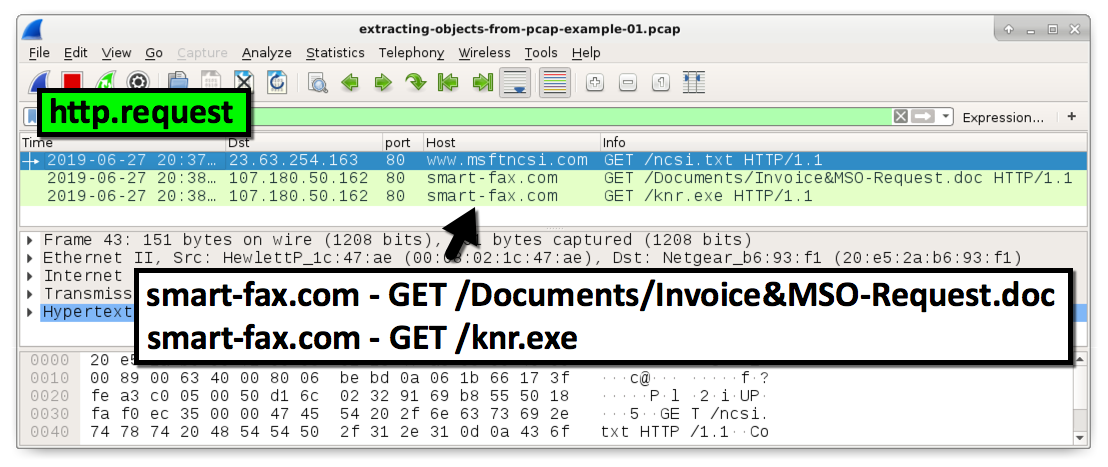 Figure 1. Filtering on the tutorial'due south first pcap in Wireshark.
Figure 1. Filtering on the tutorial'due south first pcap in Wireshark.
After filtering on http.request , find the two Go requests to smart-fax[.]com . The beginning request ends with .doctor , indicating the first request returned a Microsoft Word document. The second request ends with .exe , indicating the second request returned a Windows executable file. The HTTP GET requests are listed below.
- smart-fax[.]com - Become /Documents/Invoice&MSO-Asking.doc
- smart-fax[.]com - Go /knr.exe
We tin consign these objects from the HTTP object listing by using the menu path: File --> Export Objects --> HTTP... Figure ii bear witness this menu path in Wireshark.
 Effigy 2. Exporting HTTP objects in Wireshark.
Effigy 2. Exporting HTTP objects in Wireshark.
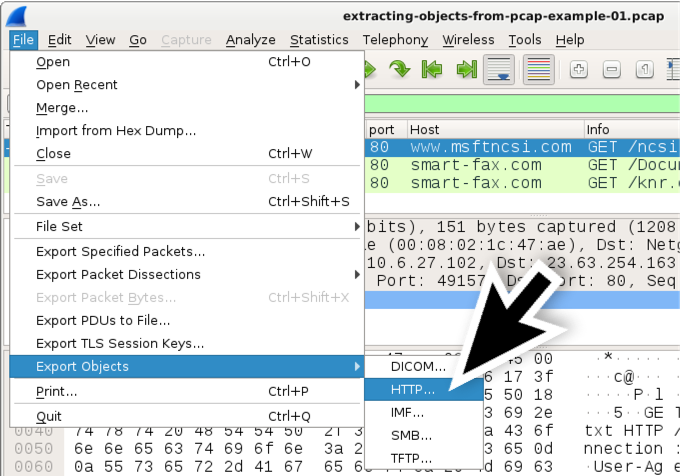
This carte du jour path results in an Export HTTP object list window as shown in Figure 3. Select the get-go line with smart-fax[.]com as the hostname and relieve information technology every bit shown in Effigy 3. Select the 2nd line with smart-fax[.]com every bit the hostname and save it as shown in Figure iv.
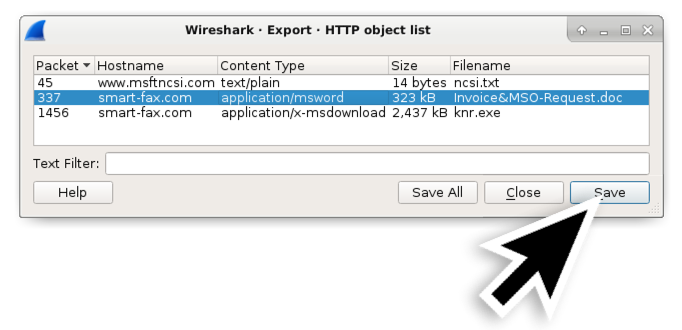 Figure 3. Saving the suspected Word document from the HTTP object list.
Figure 3. Saving the suspected Word document from the HTTP object list.
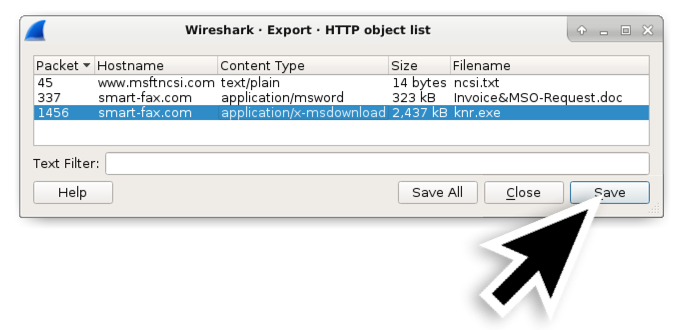 Figure iv. Saving the suspected Windows executable file from the HTTP object listing.
Figure iv. Saving the suspected Windows executable file from the HTTP object listing.
Of notation, the Content Type from the HTTP object listing shows how the server identified the file in its HTTP response headers. In some cases, Windows executables are intentionally labeled as a dissimilar type of file in an effort to avoid detection. Fortunately, the starting time pcap in this tutorial is a very straight-forrad example.
Even so, we should confirm these files are what we recollect they are. In a MacBook or Linux environment, y'all can use a terminal window or control line interface (CLI) for the following commands:
- file [filename]
- shasum -a 256 [filename]
The file command returns the type of file. The shasum command will return the file hash, in this example the SHA256 file hash. Effigy five shows using these commands in a CLI on a Debian-based Linux host.
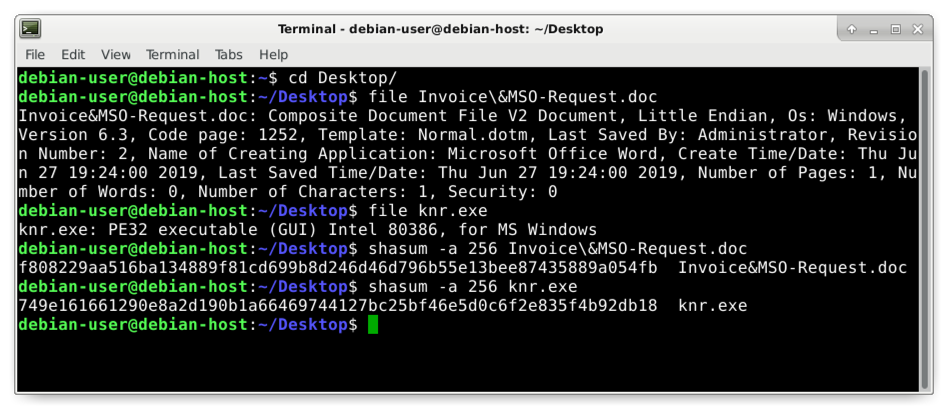 Figure 5. Determining the file blazon and hash of our ii objects exported from the pcap.
Figure 5. Determining the file blazon and hash of our ii objects exported from the pcap.
The commands and their results from Figure five are listed below:
$ file Invoice\&MSO-Request.doc
Invoice&MSO-Request.doc: Composite Document File V2 Document, Trivial Endian, Bone: Windows, Version 6.3, Code page: 1252, Template: Normal.dotm, Concluding Saved By: Administrator, Revision Number: 2, Name of Creating Application: Microsoft Role Word, Create Fourth dimension/Engagement: Thu Jun 27 19:24:00 2019, Last Saved Fourth dimension/Date: Thu Jun 27 19:24:00 2019, Number of Pages: i, Number of Words: 0, Number of Characters: 1, Security: 0
$ file knr.exe
knr.exe: PE32 executable (GUI) Intel 80386, for MS Windows
$ shasum -a 256 Invoice\&MSO-Request.doc
f808229aa516ba134889f81cd699b8d246d46d796b55e13bee87435889a054fb Invoice&MSO-Asking.doc
$ shasum -a 256 knr.exe
749e161661290e8a2d190b1a66469744127bc25bf46e5d0c6f2e835f4b92db18 knr.exe
The information above confirms our suspected Word certificate is in fact a Microsoft Word document. It likewise confirms the suspected Windows executable file is indeed a Windows executable. Nosotros can check the SHA256 hashes confronting VirusTotal to see if these files are detected every bit malware. Nosotros could also do a Google search on the SHA256 hashes to perhaps find additional information.
In addition to Windows executable or other malware files, we tin can also excerpt web pages. Our 2nd pcap for this tutorial, extracting-objects-from-pcap-instance-02.pcap (available here) contains traffic of someone inbound login credentials on a simulated PayPal login page.
When reviewing network traffic from a phishing site, we might desire to encounter what the phishing web folio looks like. Nosotros can excerpt the initial HTML page using the Export HTTP object menu as shown in Figure 6. Then we tin view information technology through a web browser in an isolated environment as shown in Figure 7.
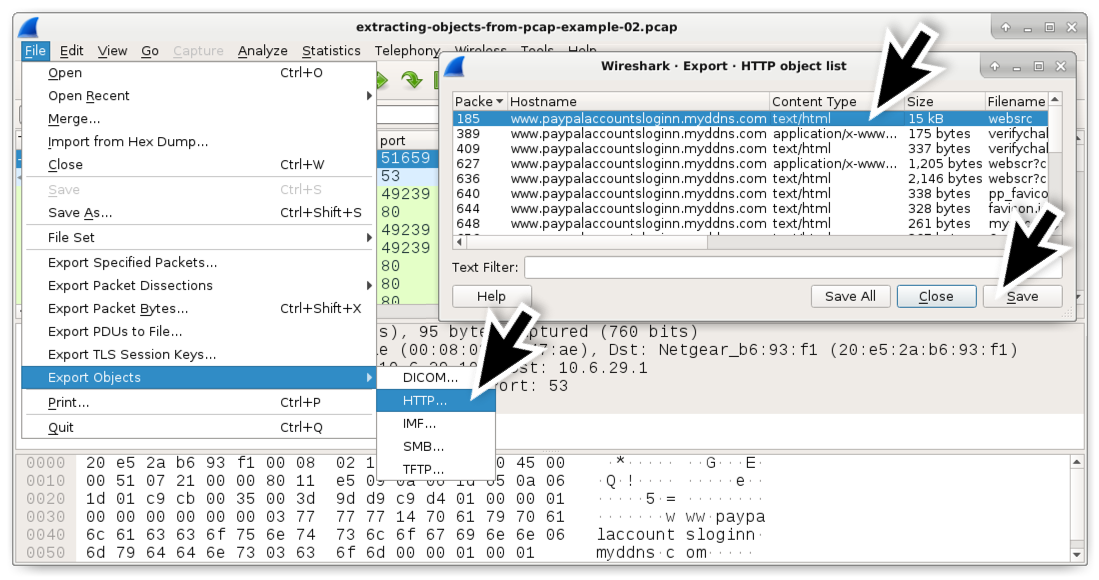 Figure 6. Exporting a simulated PayPal login page from our second pcap.
Figure 6. Exporting a simulated PayPal login page from our second pcap.
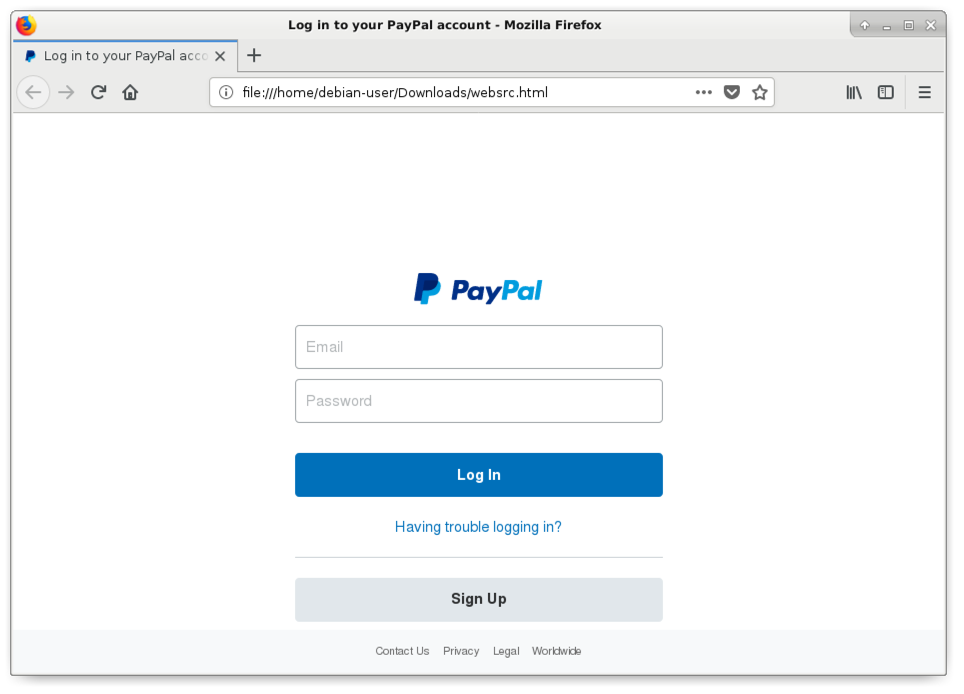 Figure 7. The exported fake PayPal login folio viewed in a web browser.
Figure 7. The exported fake PayPal login folio viewed in a web browser.
Exporting Objects from SMB Traffic
Some malware uses Microsoft'due south Server Message Block (SMB) protocol to spread across an Active Directory (Advertizement)-based network. A banking Trojan known as Trickbot added a worm module as early as July 2017 that uses an exploit based on EternalBlue to spread across a network over SMB. Nosotros continue to find indications of this Trickbot worm module today.
Our adjacent pcap represents a Trickbot infection that used SMB to spread from an infected client at ten.6.26.110 to its domain controller at 10.half dozen.26.6. The pcap, extracting-objects-from-pcap-example-03.pcap , is available here. Open the pcap in Wireshark. Use the menu path File --> Export Objects --> SMB... every bit shown in Figure 8.
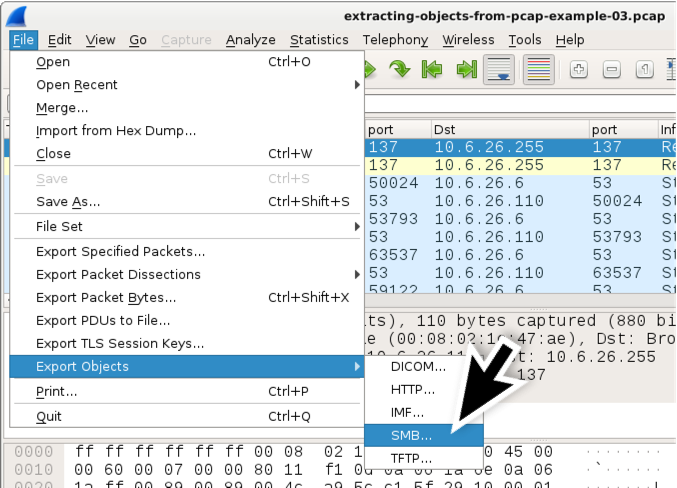 Effigy 8. Getting to the Export SMB objects list.
Effigy 8. Getting to the Export SMB objects list.
This brings upwards an Export SMB object list, listing SMB objects y'all can consign from the pcap as shown below in Figure 9.
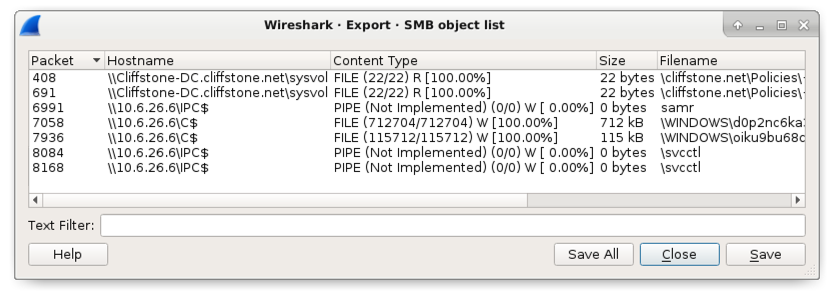 Figure 9. The export SMB object list.
Figure 9. The export SMB object list.
Notice the two entries nigh the centre of the list with \\10.6.26.6\C$ as the Hostname. A closer exam of their respective Filename fields indicates these are two Windows executable files. Encounter Table i below for details.
| Parcel number | Hostname | Content Type | Size | Filename |
| 7058 | \\10.6.26.6\C$ | FILE (712704/712704) W [100.0%] | 712 kB | \WINDOWS\d0p2nc6ka3f_fixhohlycj4ovqfcy_smchzo_ub83urjpphrwahjwhv_o5c0fvf6.exe |
| 7936 | \\x.6.26.six\C$ | FILE (115712/115712) W [100.0%] | 115 kB | \WINDOWS\oiku9bu68cxqenfmcsos2aek6t07_guuisgxhllixv8dx2eemqddnhyh46l8n_di.exe |
Table i. Data from the Export SMB objects list on the 2 Windows executable files.
In the Content Blazon column, we need [100.00%] to export a correct copy of these files. Any number less than 100 percent indicates in that location was some data loss in the network traffic, resulting in a corrupt or incomplete copy of the file. These Trickbot-related files from the pcap have SHA256 file hashes equally shown in Table 2.
| SHA256 hash | File size |
| 59896ae5f3edcb999243c7bfdc0b17eb7fe28f3a66259d797386ea470c010040 | 712 kB |
| cf99990bee6c378cbf56239b3cc88276eec348d82740f84e9d5c343751f82560 | 115 kB |
Tabular array 2. SHA256 file hashes for the Windows executable files.
Exporting Emails from SMTP Traffic
Sure types of malware are designed to plough an infected Windows host into a spambot. These spambots send hundreds of spam messages or malicious emails every infinitesimal. In some cases, the messages are sent using unencrypted SMTP, and we tin can consign these messages from a pcap of the infection traffic.
Ane such example is from our next pcap, extracting-objects-from-pcap-example-04.pcap (available here). In this pcap, an infected Windows client sends sextortion spam. Open up the pcap in Wireshark, filter on smtp.data.fragment , and you should see 50 examples of subject field lines as shown in Figure 10. This happened in five seconds of network traffic from a unmarried infected Windows host.
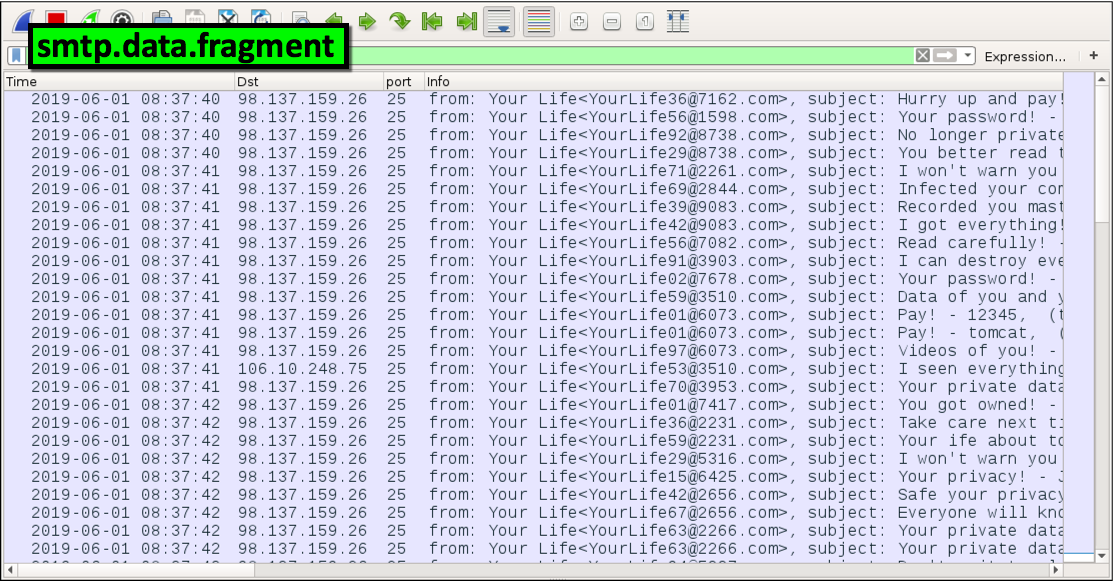 Figure ten. Filtering for email senders and subject field lines in Wireshark.
Figure ten. Filtering for email senders and subject field lines in Wireshark.
You can consign these messages using the menu path File --> Consign Objects --> Imf... as shown in Effigy 11. IMF stands for Internet Message Format, which is saved every bit a name with an .eml file extension.
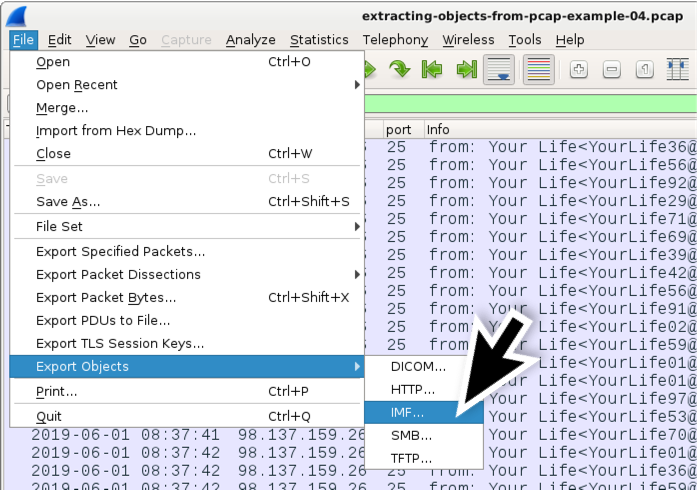 Figure 11. Exporting emails from a pcap in Wireshark.
Figure 11. Exporting emails from a pcap in Wireshark.
The sextortion spam messages are all listed with an .eml file extension in the IMF object list as shown in Figure 12.
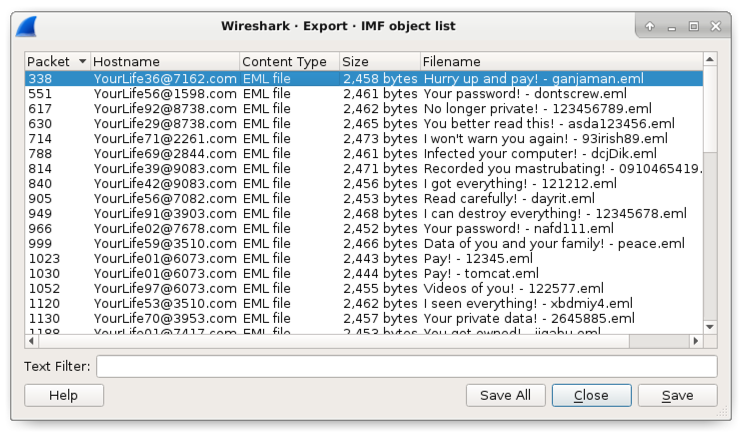 Figure 12. List of spam letters in the IMF object listing.
Figure 12. List of spam letters in the IMF object listing.
Later they are exported, these .eml files can be reviewed with an email client like Thunderbird, or they tin can exist examined in a text editor as shown in Figure xiii.
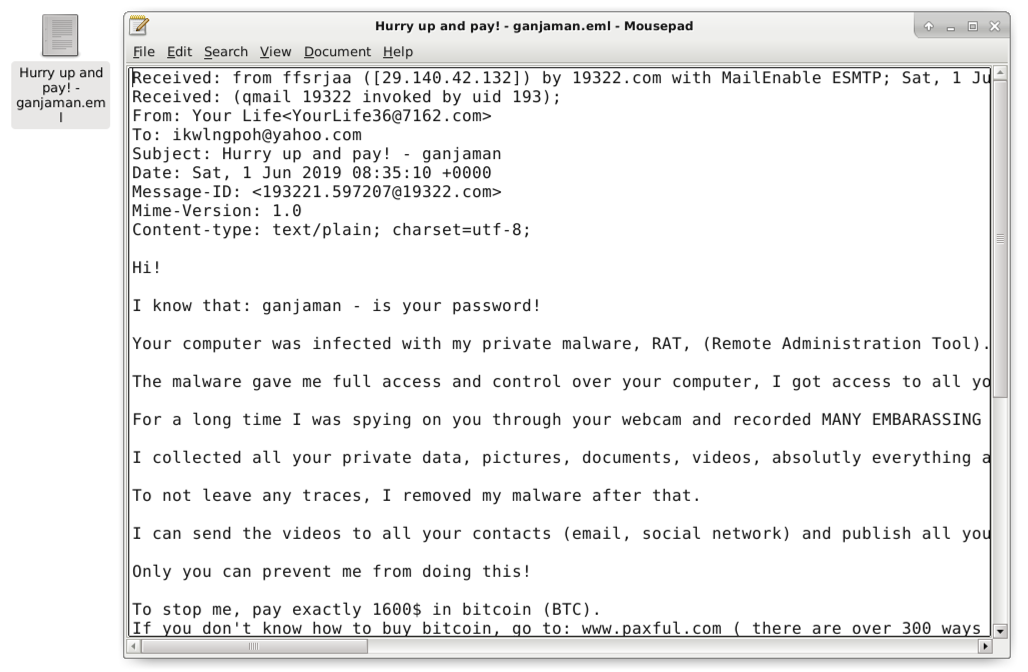 Figure 13. Using a text editor to view an .eml file exported from the pcap.
Figure 13. Using a text editor to view an .eml file exported from the pcap.
Exporting files from FTP Traffic
Some malware families use FTP during malware infections. Our side by side pcap has malware executables retrieved from an FTP server followed by information from the infected Windows host sent back to the same FTP server.
The next pcap is extracting-objects-from-pcap-example-05.pcap and is available here. Open up the pcap in Wireshark. Filter on ftp.asking.control to review the FTP commands every bit shown in Effigy fourteen. You lot should discover a username (USER) and countersign (Laissez passer) followed past requests to remember (RETR) five Windows executable files: q.exe , due west.exe , e.exe , r.exe , and t.exe . This is followed by requests to store (STOR) html-based log files back to the same FTP server approximately every xviii seconds.
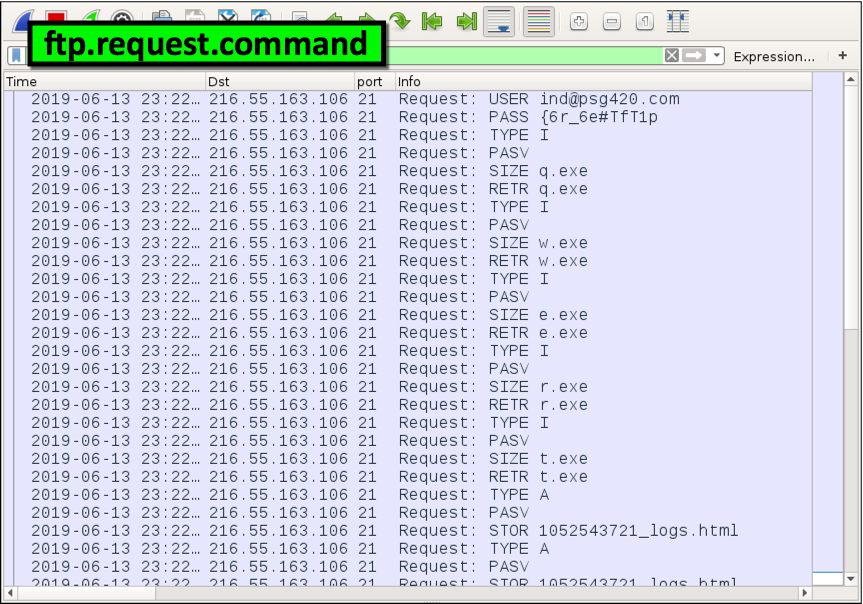 Figure 14. Filtering for FTP requests in Wireshark.
Figure 14. Filtering for FTP requests in Wireshark.
At present that we have an thought of the files that were retrieved and sent, nosotros can review traffic from the FTP data channel using a filter for ftp-data as shown in Figure fifteen.
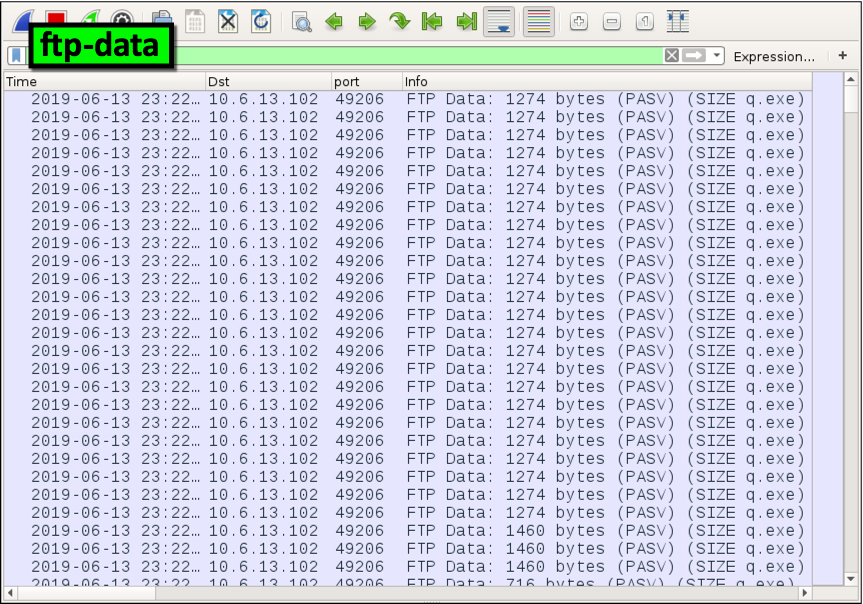 Figure xv. Filtering on FTP information traffic in Wireshark.
Figure xv. Filtering on FTP information traffic in Wireshark.
We cannot utilize the Export Objects function in Wireshark to export these objects. All the same, we can follow the TCP stream from the data channels for each. Left-click on any of the lines that end with (SIZE q.exe) to select i of the TCP segments. So right-click to bring up a menu and select the menu path for Follow --> TCP stream equally shown in Figure xvi.
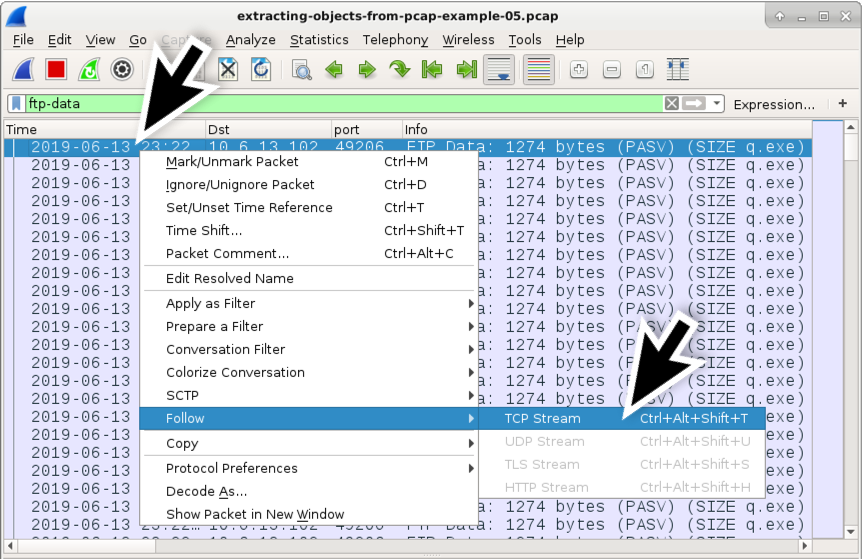 Figure xvi. Following the TCP stream of an FTP data aqueduct for q.exe .
Figure xvi. Following the TCP stream of an FTP data aqueduct for q.exe .
This volition bring up the TCP stream for q.exe over the FTP data channel. Near the bottom of the window is a button-style carte du jour labeled "Testify and save data as" which defaults to ASCII as shown in Effigy 17. Click on the menu and select "Raw" equally shown in Effigy eighteen.
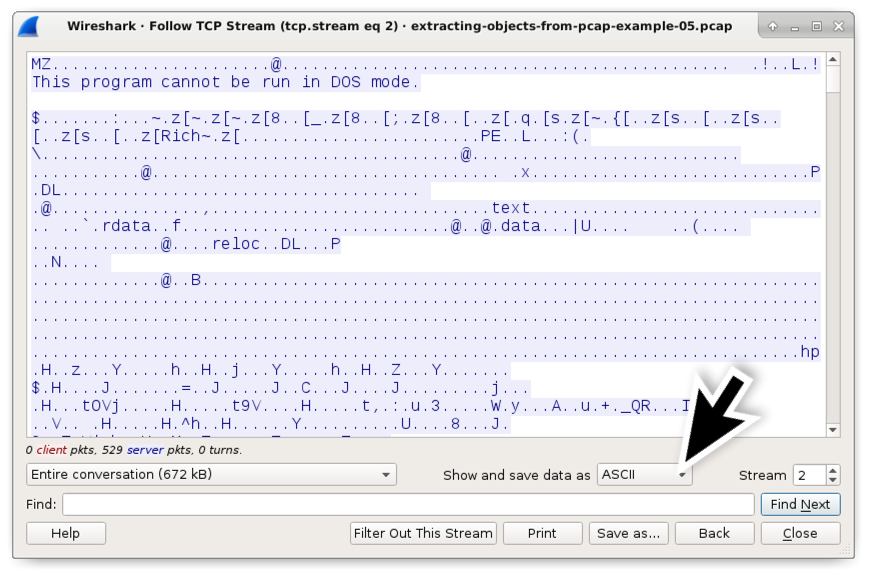 Effigy 17. The TCP stream window for q.exe . Notation the "Show and relieve information every bit" button-style bill of fare.
Effigy 17. The TCP stream window for q.exe . Notation the "Show and relieve information every bit" button-style bill of fare.
 Figure 18. Selecting "Raw" from the "Prove and relieve data as" bill of fare.
Figure 18. Selecting "Raw" from the "Prove and relieve data as" bill of fare.
The window should now show hexadecimal characters instead of ASCII equally shown in Figure 19. Employ the Save equally... button near the bottom of the window to save this as a raw binary, besides shown in Figure 19.
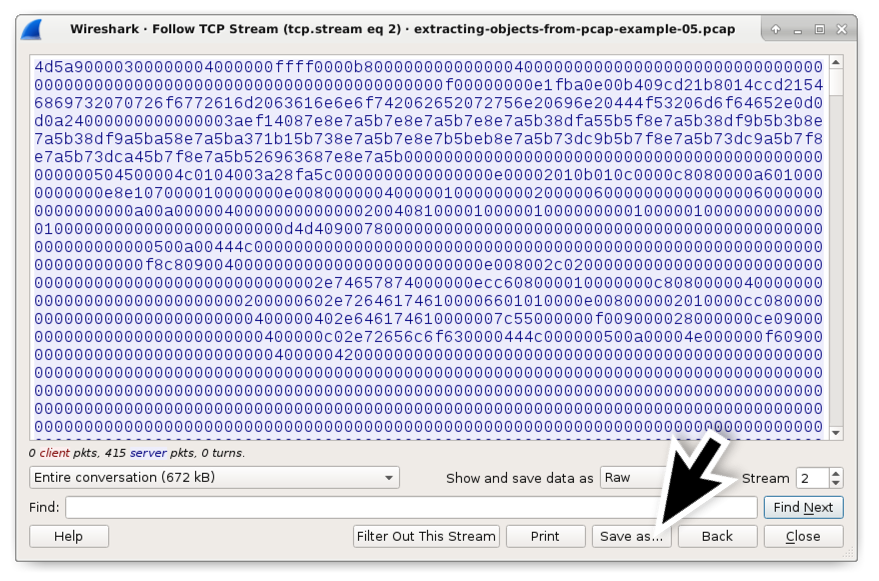 Effigy 19. Saving the data from a TCP stream equally a raw binary.
Effigy 19. Saving the data from a TCP stream equally a raw binary.
Save the file equally q.exe . In a Linux or like CLI environment, confirm this is a Windows executable file and get the SHA256 hash equally shown below.
$ file q.exe
q.exe: PE32 executable (GUI) Intel 80386, for MS Windows
$ shasum -a 256 q.exe
ca34b0926cdc3242bbfad1c4a0b42cc2750d90db9a272d92cfb6cb7034d2a3bd q.exe
The SHA256 hash shows a high detection rate as malware on VirusTotal. Follow the same procedure for the other .exe files in the pcap:
- Filter on ftp-information
- Follow the TCP stream for a TCP segment with the name of your file in the Info cavalcade
- Change "Show and salve data as" to "Raw"
- Utilize the "Save as..." push to save the file
- Check to make sure your saved file is, in fact, a Windows executable file.
This should give you the following files as shown below in Table three.
| SHA256 hash | File proper noun |
| 32e1b3732cd779af1bf7730d0ec8a7a87a084319f6a0870dc7362a15ddbd3199 | e.exe |
| ca34b0926cdc3242bbfad1c4a0b42cc2750d90db9a272d92cfb6cb7034d2a3bd | q.exe |
| 4ebd58007ee933a0a8348aee2922904a7110b7fb6a316b1c7fb2c6677e613884 | r.exe |
| 10ce4b79180a2ddd924fdc95951d968191af2ee3b7dfc96dd6a5714dbeae613a | t.exe |
| 08eb941447078ef2c6ad8d91bb2f52256c09657ecd3d5344023edccf7291e9fc | w.exe |
Table 3. Executable files from the FTP traffic.
Nosotros have to search more precisely when exporting the HTML files sent from the infected Windows host back to the FTP server. Why? Considering the same file name is used each fourth dimension. Filter on ftp.request.command , and scroll to the end. Nosotros tin see the same file name used to store (STOR) stolen data to the FTP server as an HTML file as shown in Effigy 20.
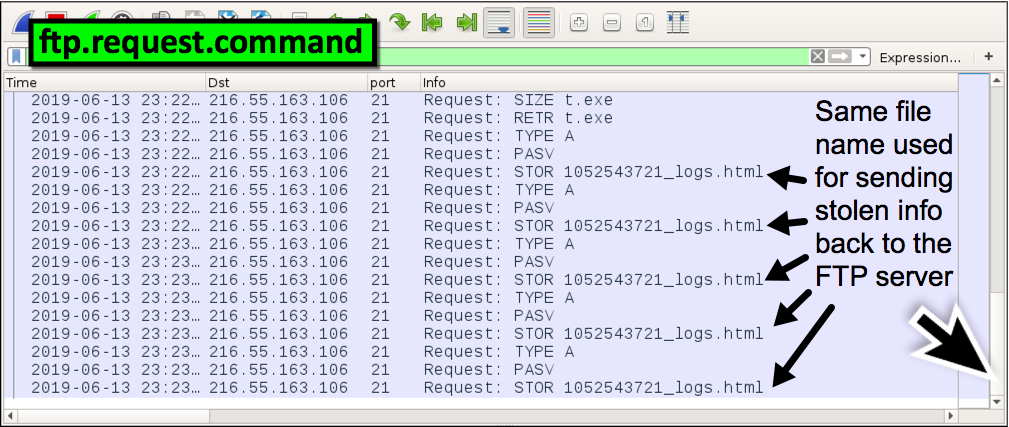 Effigy xx. The same file name used for sending stolen info back to the FTP server.
Effigy xx. The same file name used for sending stolen info back to the FTP server.
To see the associated files sent over the ftp information aqueduct, use the filter ftp-data.control contains .html as shown in Figure 21.
 Effigy 21. Filtering on files with .html in the file name over the FTP data channel.
Effigy 21. Filtering on files with .html in the file name over the FTP data channel.
In Effigy 21, the destination port changes each time the file is stored (STOR) to the FTP server. The first time has TCP port 52202. The 2d time has TCP port 57791. The third time has TCP port 55045. The fourth time has 57203. And the 5th time has 61099.
We utilize the same process as before. Instead of focusing on the file names, focus on the TCP ports. Follow the TCP stream for any of the TCP segments using port 52202. In the TCP stream window, alter "Show and salve data as" to "Raw." Then save the file. Do the same for the HTML file over TCP port 57791.
If you practice this for all five HTML files, you'll find they are the same exact file. These text-based HTML files comprise information about the infected Windows host, including any passwords plant by the malware.
Summary
Using the methods outlined in this tutorial, we can excerpt various objects from a pcap using Wireshark. This can be extremely helpful when you need to examine items from network traffic.
For more than help using Wireshark, please see our previous tutorials:
- Customizing Wireshark - Changing Your Column Display
- Using Wireshark: Display Filter Expressions
- Using Wireshark: Identifying Hosts and Users
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from u.s.a.
How To Find A Command And Control Service Traffic In Pcap File,
Source: https://unit42.paloaltonetworks.com/using-wireshark-exporting-objects-from-a-pcap/
Posted by: fergusonsuffect.blogspot.com


0 Response to "How To Find A Command And Control Service Traffic In Pcap File"
Post a Comment